Don’t Let Your Wi-Fi Be a Sitting Duck: A Beginner’s Guide to Dodging Denial-of-Service (DoS) Attacks!
Alright, fellow cyber-citizens, buckle up your digital seatbelts because we’re about to dive into the crazy world of denial-of-service (DoS) attacks! Imagine this: you’re lounging on your couch, binge-watching your favourite show, and suddenly *poof*—your internet connection vanishes like a magician’s bunny! What in the world just happened? Well, my friends, you might have just become the unwitting victim of a DoS attack.
The following threats highlight the potential impact of DoS attacks on the availability, integrity, and security of devices and their associated services. Let’s break it down, shall we?
Volume-based Attacks
These flood the target network with a high volume of traffic, such as UDP flood attacks, ICMP flood attacks, or SYN flood attacks.
Ever heard of a frat party where uninvited guests flood in, hog all the snacks, and leave nothing for the poor souls who actually live there? That’s pretty much what a volume-based DoS attack does to your internet connection. Picture your router as the host, and suddenly, it’s inundated with a deluge of fake traffic, overwhelming its capacity like a chipmunk trying to eat an entire pizza. Your poor router is left gasping for bandwidth, and you’re left staring at the dreaded loading wheel of doom.
Resource Exhaustion
DoS attacks can deplete system resources such as CPU, memory, bandwidth, or network connections, making the device unable to respond to legitimate requests.
It’s like having a hundred kids simultaneously asking you for snacks while you’re trying to cook dinner—eventually, you’re going to run out of snacks, patience, or both! In a DoS attack, cyber-criminals exploit vulnerabilities in our network, gobbling up our resources faster than you can say “upgrade to fibre optic.”
Network Disruption
Devices targeted by DoS attacks may experience network congestion or saturation, leading to disruptions in communication and connectivity for both the targeted device and other devices on the same network.
Imagine a busy intersection suddenly flooded with chickens on unicycles—utter chaos! Similarly, a DoS attack can disrupt your network traffic, turning your smooth data highway into a gridlocked nightmare. Good luck streaming Netflix when your data packets are stuck in bumper-to-bumper traffic!
Service Unavailability
When overwhelmed by a DoS attack, devices may become unresponsive or slow to respond to valid requests, rendering services inaccessible to genuine users.
Ever tried ordering pizza during a blackout? Not gonna happen! Similarly, a DoS attack can render your favourite online services as elusive as Bigfoot on roller skates. No email, no social media, just the sweet sound of digital crickets chirping.
Data Loss or Corruption
In some cases, DoS attacks may result in data loss or corruption, especially if the targeted device is unable to handle the influx of data or if the attack aims to exploit vulnerabilities in data handling processes.
It’s like your digital files took a stroll through the Bermuda Triangle—gone without a trace! A DoS attack can wreak havoc on your precious data, leaving you scratching your head and wondering if your dog really did eat your report that your boss expects tomorrow morning.
Secondary Attacks
DoS attacks can sometimes serve as a distraction or cover for other malicious activities, such as data breaches, malware injections, or unauthorized access attempts, taking advantage of the chaos caused by the attack to carry out additional threats.
It’s similar to getting hit by a snowball, then realizing it’s just the precursor to an avalanche! Once cyber-criminals breach your defences with a DoS attack, they might just stick around for the afterparty, launching even sneakier attacks while you’re still reeling from the first blow.

Limited Edition – Get it while it’s hot!
Motives Behind the Madness
Now, why would anyone unleash this digital chaos upon innocent households like yours? Well, folks, the motives are as varied as the toppings on a pizza. Maybe it’s a disgruntled former roommate seeking revenge for stealing their last slice. Or perhaps it’s a shady competitor trying to sabotage your burgeoning online knitting empire. Heck, it could even be a bored teenager with too much time and too little adult supervision!
DoS attacks can be used for various purposes, depending on the motives of the attacker. Some common reasons why these attacks are utilized include:
- Disrupt the normal operation of targeted services or systems. By overwhelming the target with a flood of traffic, the attacker can make it inaccessible to legitimate users, causing inconvenience, financial losses, and reputational damage to the victim.
- The extorting of money from the victim. They may threaten to continue the attack unless a ransom is paid, leveraging the threat of prolonged disruption to coerce the victim into compliance.
- Hacktivist groups or individuals may use DoS attacks as a form of protest or to advance a particular political or ideological agenda. By targeting websites or services associated with their adversaries, they aim to disrupt their operations or convey a message to the public.
- A competitor within an industry, may resort to DoS attacks against their rivals to gain a competitive advantage. By disrupting the online presence or services of competitors, they seek to undermine their business operations and market position.
- Ethical hackers (Pen Testers), security researchers, or malicious actors may use DoS attacks to test the resilience of systems or network defences against such attacks. By identifying vulnerabilities and weaknesses, organizations can take proactive measures to strengthen their security posture and mitigate the risk of future attacks.
Overall, the motives behind DoS attacks can vary widely, ranging from financial gain and ideological motivations to competitive advantage and security testing. Regardless of the intent, these attacks can have significant repercussions for the targeted individuals, organizations, and even entire communities.
Prevention is Key
Preventing denial-of-service (DoS) attacks requires a multi-layered approach that addresses vulnerabilities at various levels of the network infrastructure and application stack.
So, how do you protect your digital fortress from these nefarious attacks? Fear not, brave netizen, for I shall now bestow upon you the sacred scrolls of cyber-defence! Here are several ways to prevent or mitigate the impact of DoS attacks:
1. Fortify Your Fortress: Update your devices regularly including your router firmware faster than you can say “supercalifragilisticexpialidocious.” Stronger defences mean fewer chinks in your digital armour.
2. Bandwidth Bodyguards: Invest in a robust firewall and intrusion detection system to keep those pesky cyber-hooligans at bay. It’s like hiring a bouncer for your data party! Avast Firewall lets you know the apps that are active, inactive or blocked on your device. You can also see which network you are connected to now and which ones you were connected to in the past. The logs show time and date as well as other details of blocked apps.
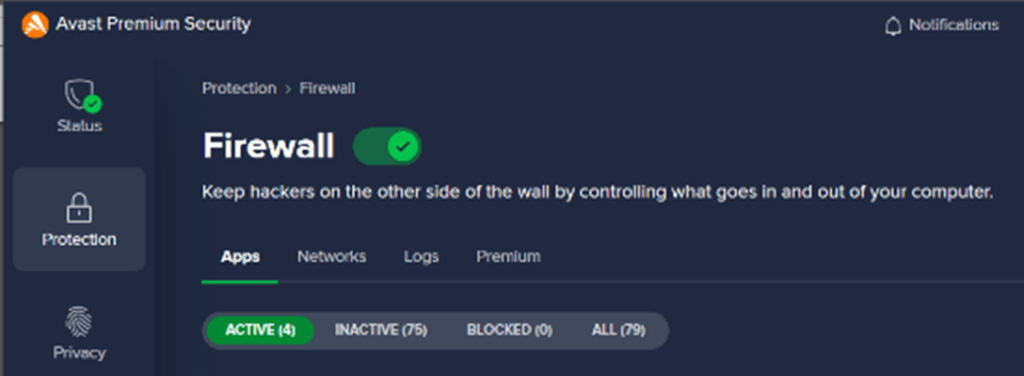
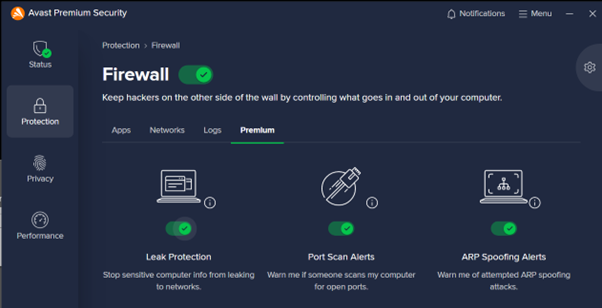
Premium customers also get leak protection, port scan and ARP spoofing alerts.
3. Stay Vigilant: Keep an eagle eye on your network traffic like a hawk stalking its prey. Suspicious network connections viewed in your firewall could be a red flag waving in the digital breeze.
4. Backup, Backup, Backup: Just like a squirrel hoarding acorns for winter, always keep backups of your important data. That way, even if disaster strikes, you’ll be back up and running in no time.
5. Education is Power: Arm yourself with knowledge like a cyber-samurai wielding a pixelated katana. Stay informed about the latest threats and arm yourself with the tools to combat them.
There you have it, fellow cyber-warriors! Armed with this knowledge, you shall fear no DoS attack, for you are the guardians of your digital domain!
By implementing these preventive measures and adopting a proactive approach to security, individuals and organizations can significantly reduce their exposure to denial-of-service attacks and minimize the impact of any potential incidents.
Now, go forth and surf the web with confidence, knowing that your computer network is no longer a sitting duck but a mighty fortress of digital resilience!






The article provides a comprehensive analysis of denial-of-service (DoS) assaults, including their traits, manifestations, and effects. It makes technical information easy to understand so that readers can better understand cyber risks. The post also offers doable advice for preventing denial-of-service (DoS) assaults, highlighting the importance of strong security procedures and proactive threat detection.
Heya Kiersti
Your comment is insightful! I’m thrilled to hear that you found the article’s analysis of denial-of-service (DoS) assaults clear and comprehensive. One of my main goals is to make technical information accessible and understandable, so it’s great to know that this approach helped you better grasp the nuances of cyber risks.
Indeed, DoS attacks can be complex and devastating, but with the right knowledge and tools, they can be effectively mitigated. Strong security procedures and proactive threat detection are critical in this ongoing battle. It’s all about staying one step ahead of potential attackers by implementing robust defences and continuously monitoring for any unusual activity.
I’m glad you found the advice practical and actionable. By taking these steps, both individuals and organizations can significantly reduce their vulnerability to DoS attacks and other cyber threats.
Thank you again for your feedback and for highlighting the key points of the article. Let’s keep working together to build a safer digital environment for everyone!
Continue to protect yourself in the cybersphere!
Khalil
Education is 100 % key. I also think that empowering individuals with knowledge about the latest threats is crucial in the ongoing battle against cyber-attacks.
I dont think people are awear on how important investing in a good firewall or malware protection is.
Overall, this comprehensive approach to cybersecurity provides valuable insights for both individuals and organizations seeking to safeguard their digital assets. Great read, Well done!
Hi Clair
Thank you so much for your thoughtful comment! I couldn’t agree more – education is absolutely crucial in the fight against cyber-attacks. Empowering individuals with up-to-date knowledge about the latest threats truly makes a difference in enhancing our collective cybersecurity posture.
You’re spot on about the importance of investing in good firewall and malware protection. Many people underestimate these tools, but they are fundamental in defending against a wide range of cyber threats. A strong firewall acts as a barrier between your computer and malicious traffic, while effective malware protection can detect and neutralize threats before they cause harm.
It’s great to hear that you found the comprehensive approach to cybersecurity in the article valuable. Spreading awareness and encouraging proactive measures are key steps we can all take to safeguard our digital assets, both personally and professionally.
Thank you again for your kind words and for contributing to the discussion. Let’s continue to advocate for cybersecurity education and make sure everyone understands the importance of these protective measures!
Be safe out there!
Khalil
I was wondering is a DOS attack similar or the same as a virus attack? I have never heard of DOS attacks until I read this article, so was just wondering as the two sound almost the same with the same symptoms.
You have given some great advice about protecting yourself against these attacks like using Firewalls and also updating regularly, which we are all guilty of avoiding when we are busy.
Backing up your data is also very important, not only for these sorts of attacks, but even if your hard drive fails you.
Hello Michel,
Great question! It’s easy to see why there might be some ambiguity between DOS attacks and virus attacks, because a virus can be used to carry out a complex DOS attack. But they can be quite different in their nature and impact.
In a DOS attack, the attacker overwhelms a network or website with so much traffic that legitimate users can’t access it. It’s not about spreading harmful code; it’s about making a service unavailable by flooding it with bogus requests.
On the other hand, a virus attack is a type of malicious software that, once it infects your computer, can replicate itself and spread to other systems. It can steal data, corrupt files, or even take control of your computer. The key difference is that a virus infects and damages systems by inserting malicious code, whereas a DOS attack disrupts service by overwhelming the network.
I hope this clears things up! If you have any more questions or need further clarification, please feel free to ask. Stay safe online!
Thanks for your comment Michel
Khalil